Do You Really Want To Know Why Your Antivirus Program Didn’t Protect You?
 I won’t say I’ve heard it all, but I have heard enough. Enough from customers that have asked me how did my computer get infected, I’ve got Norton, or McAfee, or whatever. Aren’t they some of the best virus and spyware protection products on the market? Without getting into any preferences for antivirus software, many of the good ones still fall short when it comes to detecting zero-day threats. Even the best of the best just can’t detect them all. And don’t forget the obvious, that some people have absolutely no antivirus software at all, while others’ is expired, or hasn’t been updated. Then there are just some that are extremely high-risk internet surfers that can’t lay off the adult and pirated software websites that are saturated with malware. But what you can do about it will require you to read and understand a bit about zero-day threats and how we need a new approach to computer security, one that is actually opposite to what you have been using. Its actually not new, its just not what became the accepted standard. We have been a bunch of cows going over the cliff for far too long now.
I won’t say I’ve heard it all, but I have heard enough. Enough from customers that have asked me how did my computer get infected, I’ve got Norton, or McAfee, or whatever. Aren’t they some of the best virus and spyware protection products on the market? Without getting into any preferences for antivirus software, many of the good ones still fall short when it comes to detecting zero-day threats. Even the best of the best just can’t detect them all. And don’t forget the obvious, that some people have absolutely no antivirus software at all, while others’ is expired, or hasn’t been updated. Then there are just some that are extremely high-risk internet surfers that can’t lay off the adult and pirated software websites that are saturated with malware. But what you can do about it will require you to read and understand a bit about zero-day threats and how we need a new approach to computer security, one that is actually opposite to what you have been using. Its actually not new, its just not what became the accepted standard. We have been a bunch of cows going over the cliff for far too long now.
Zero-Day Threats
You are probably familiar with having to install Microsoft Windows Updates. But did you know that most major software vendors provide updates and patches for their software as well? Some of these updates are just enhancements to the program, while others are security updates to patch vulnerabilities or software holes that might allow malicious code to be executed on your computer. Some of these exploits might be well known already, even to the point of having a signature, making it possible for the antivirus companies to create a virus definition for it, or a blacklist. In this case, your antivirus program may protect you against exploits to a particular vulnerability, even though the vulnerable program hasn’t been immunized with a security update yet. This is where multi-layered protection comes in. But what about exploits that have no known signature yet? What if the vulnerability itself isn’t even known about yet? This is a critical area of computer security that often gets ignored by most people, one we call zero-day threats.
A simple definition of a zero-day vulnerability is based on a time frame from when a software vulnerability is discovered until the time the solution or patch is made public. Imagine a malicious code writer (or a hacker) that discovers an unpatched computer security vulnerability before the software vendor even knows about it. It happens all the time, and not just with the Windows Operating System, but with all types of programs. I don’t know if they use the term zero-day in the medical field, but Polio had a 46 year zero-day from the time it was discovered in 1909 until 1955 when the vaccine was made public. Who knows how long it went undiagnosed before that.
But even for vulnerabilities the software vendors might already be privy to, this information still might not have been released to the public, especially if they haven’t devised a solution yet. As much as I would like the antivirus industry to be able to catch 100% of the threats out there, its not each antivirus vendors job to fix holes with other company’s software. As such, if the vulnerability hasn’t been made public yet, the antivirus vendors might still be in the dark about it.
So what can you do? The zero-day threat window can be days to even weeks. I think it is very obvious that the whole approach of catching a fish before you can tell what kind of fish it is doesn’t work too well for computer security. Maybe a skilled fisherman can tell what kind of fish it is before he lands it by how it bites, and how it fights, like antivirus with heuristics can. But even antivirus software with advanced heuristic detection features can’t detect every instance of unknown malicious software. For the most part, antivirus and antispyware software rely entirely on blacklists. What it knows, it can detect … maybe. So what other approach to computer security is there?
Blacklist vs Whitelist Protection
If the security software you are using to stucco over the holes in other software has holes in itself, why do we keep buying it? I know, its what we have been told and its all we know to do. I am a victim of the system too, although I have done well with blacklist protection coupled with some advanced knowledge of how to manually avoid the threats. But I have finally found the solution I have been looking for, one for everyday people that most anybody can learn to use very quickly.
So are you ready for a paradigm shift in the approach you have been taught as the only way to secure a computer? If blacklisting can only block what it knows is bad, why not only allow what we know is good and just block the rest? This is called whitelisting. But I wouldn’t dump my antivirus software just yet, so I suggest that you use both blacklist and whitelist protection.
Imagine starting off with a clean computer and keeping it that way by automatically scanning your computer and whitelisting all your existing “known good” programs. From then on, you can manage any new programs with your whitelist when you try to install or run them by approving them with a password. If you don’t whitelist them, they won’t run. This gives you all the time you need to do your homework and scan any suspect files and programs you may have downloaded before you attempt to run and approve them. The only hole to this system is you, if you let it run that is, but that is what your antivirus software is there for, to catch the crumbs you accidentally dropped.
The Solution is Faronics Anti-Executable
So the polar opposite to blacklisting, known as whitelisting allows only an approved collection of programs that were deemed safe to run on your computer. Application whitelisting for the 21st Century has evolved into a modern solution that offers a flexible and easy-to-use platform for today’s dynamic environments. Faronics Anti-Executable provides advanced endpoint protection and makes managing lists of sanctioned programs a breeze.
Your current Antivirus software uses blacklisting technology to protect against known threats by banning them based on a master list. The alarming frequency and complexity of new malware development creates a serious lag between inception and detection. Chasing after tens of thousands of new malware pieces every day leaves you in a vulnerable position, especially given antivirus’s inability to protect against zero-day and targeted attacks. Faronics Anti-Executable fills in the gaps by stopping unauthorized and malicious software from installing on your machine giving you the ultimate protection while in-session.
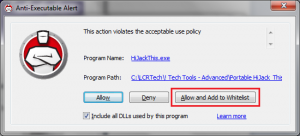
Below is a screenshot of an alert I got when trying to run I program I know is safe that I had not whitelisted yet. I immediately got this alert which gave me some choices to Allow or Deny it. I chose to “Allow and Add to Whitelist” so I won’t be bothered again for this program I know I trust.
While there are a few different versions of Faronics Anti-Executable, the “Standard” version called “Faronics Anti-Executable Standard” is the version suitable for most home and small business users. It is quite affordable! If you have Server or Enterprise requirements or would like to try some other Faronics products, visit the Faronics Product Catalog.

Buy Faronics Anti-Executable Standard – One Year Subscription


2 Responses to “Do You Really Want To Know Why Your Antivirus Program Didn’t Protect You?”
[…] is full of holes. Especially when you consider unknown or zero-day threats. See the article “Do You Really Want to Know Why Your Antivirus Program Didn’t Protect You” for more information about zero-day threats, blacklisting and its more effective […]
[…] online internet security and computer health. To learn about a superb whitelisting product, click Virus and Spyware Protection for more […]
Leave a Reply